Looking to bolster online safety and security? Maybe you want to explore geo-restricted websites and content or simply save something when shopping online or buying flight tickets. VPN services are often promoted as a solution for such issues. They mask internet connections allowing users to browse the internet without being tracked.
Even internet service providers aren’t able to throttle the connection when exploring bandwidth-intensive MOBA games. Although VPNs or virtual private networks mask IP addresses and keep browsing data private, they’re not immune to security threats. In fact, some threats and ransomware are designed to specifically target vulnerable VPNs Here’s what to know about VPN security and breaches:
How VPNs Work
Personal and business VPN services allow access to remote computers or servers that let users browse the internet as if they live where the remote server is located. For instance, Ontario is the only province in Canada with a legal framework for licensing third-party casinos. Players can freely explore the online casinos in Canada to enjoy slots, roulette, blackjack, craps, poker, live dealer games, and more. Those outside Ontario are limited to provincial casinos that have few games and bonuses. However, with a VPN service, they can enjoy casinos licensed outside their province without breaking any rules.

Simply subscribe to a VPN service, install the app on a phone or computer, choose Ontario or another location with legal gambling, and connect to the servers. Once connected, players can then explore the casinos licensed in those areas. The same goes for blocked content and global services. VPNs offer secure internet access tunnels that hide various browsing details. They encrypt internet connections and route them to a random third-party server with a random IP address in the chosen location. The server acts as the middleman between user devices and the internet or websites they want to access, allowing them to bypass geo-restrictions. Mobile and remote access VPNs also connect to remote networks instead of public internet.
Types of VPN Vulnerabilities
VPN breaches usually occur as data leaks and backdoors, or entry points, that allow hackers to access unauthorized networks, files, and resources. Breaches may also stem from using free services with bad logging practices. Such businesses track internet activity and steal data or bandwidth, selling them to the highest bidders. Fortunately, VPN users can avoid poor logging practices by choosing authentic paid VPN services. VPN leaks are often a result of connection failure, mismatched or improper OS configuration, and outdated security features or protocols. Failed connection issues can be fixed by activating the kill switch, which automatically shuts down all internet connections.
Kill switches only allow access to a website once a connection to the remote server has been established, eliminating the window for IP address leaks. Improper or mismatched configurations, like using a VPN that doesn’t permit IPv6 connection on an operating system with enabled IPv6 connectivity, may also result in DNS data leaks. Proper configuration and choosing more secure protocols like PPTP over L2T can help prevent such data leaks. Outdated VPN software and security protocols also leave room for hackers. Leading VPN services offer automatic security updates and patches to address emerging threats. Users can update their computers and install security patches as soon as they’re recommended by the VPN provider. Updating the software, VPN servers, firewalls, and routers limit exposure to attacks.
Dealing With VPN Breaches
Managing VPN breaches involves proactive measures, ongoing monitoring, and quick response. Proactive measures include subscribing to credible paid VPN services, installing the latest VPN software and security patches, activating the kill switch, and configuring the VPN correctly. Other measures include split tunneling, add blockers, and Wire Guard protocol to protect VPN users from popular threats. Ongoing monitoring involves tracking network activity, outgoing pings, logins, and resource access to spot hackers and malware before they cause a major breach. Thanks to AI, machine learning, and behavioral analytics, VPN users can track their networks and connections using a simple dashboard with all the important security analytics.
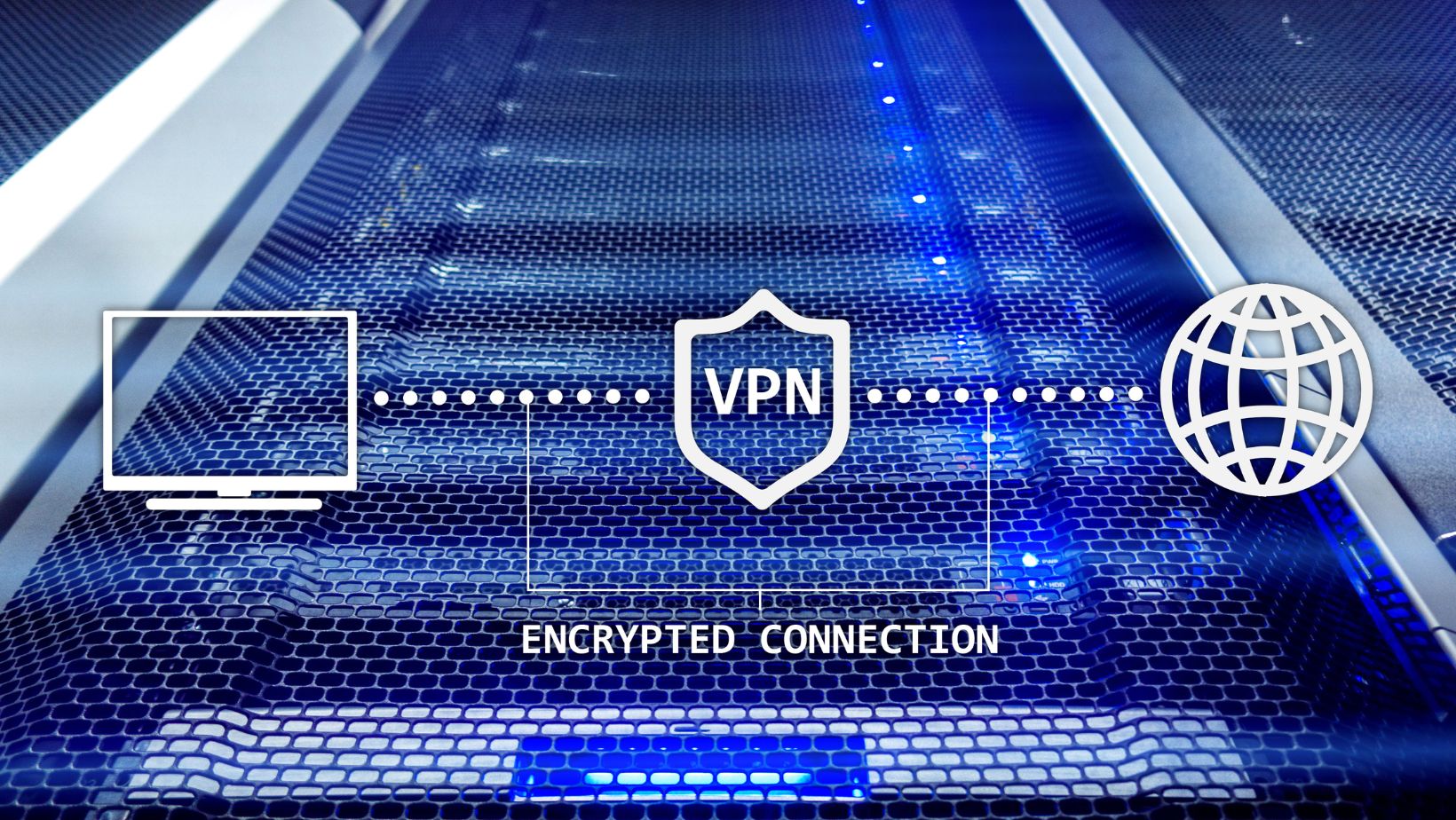
The AI systems autonomously monitor logins, durations, accessed locations and resources, and other parameters to identify suspicious activity. Flagged activity is blocked immediately and a notification is sent to the cybersecurity team for further investigation. AI also learns from interactions and establish a baseline pattern to help flag suspicious invasions. Monitoring also helps spot low-volume and high-volume DDoS attacks before they’re fully fledged, giving users time to mitigate the damage and prevent lengthy downtimes. VPN users should also establish a quick-response protocol to follow in case of an attack. Some measures include backing up data, updating passwords and credentials, and notifying the provider of the suspected breach.
The Future VPNs and Cybersecurity
VPNs have maintained their spot as the ideal solution for masking IP addresses and securing internet connections. As technology advances, artificial intelligence, blockchain, and machine learning are quickly being deployed to further enhance security. Nonetheless, attacks have also become more sophisticated and discrete, making the hunt for total security a never-ending race between cybersecurity teams and hackers. For users, the best way to remain secure is through using leading VPN services, automating security updates, and proactive monitoring.